Web threat
|
Read other articles:

この記事は検証可能な参考文献や出典が全く示されていないか、不十分です。出典を追加して記事の信頼性向上にご協力ください。(このテンプレートの使い方)出典検索?: コルク – ニュース · 書籍 · スカラー · CiNii · J-STAGE · NDL · dlib.jp · ジャパンサーチ · TWL(2017年4月) コルクを打ち抜いて作った瓶の栓 コルク(木栓、蘭&…

Look up tailpiece in Wiktionary, the free dictionary. This violin tailpiece has one fine tuner on the E string. Bass guitar tailpiece A tailpiece is a component on many stringed musical instruments that anchors one end of the strings, usually opposite the end with the tuning mechanism (the scroll, headstock, peghead, etc.). Function and construction Mandolin tailpiece, which simply anchors the strings solidly The tailpiece anchors the strings, so it must be strong enough to withstand their combi…
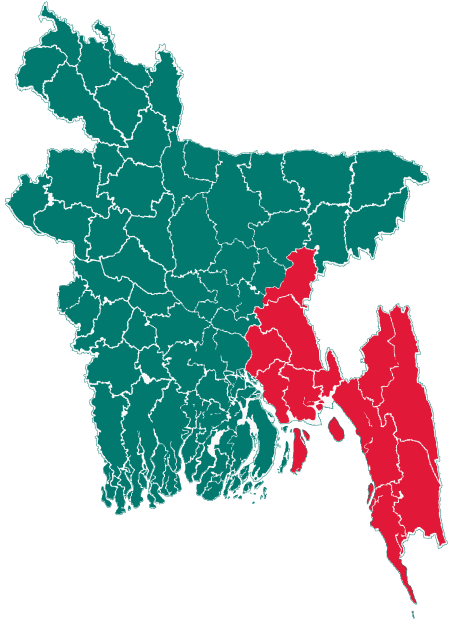
Upazila in Chittagong, BangladeshThanchi থানচিUpazilaAmiakhum FallsCoordinates: 21°47.2′N 92°25.7′E / 21.7867°N 92.4283°E / 21.7867; 92.4283Country BangladeshDivisionChittagongDistrictBandarbanArea • Total1,020.82 km2 (394.14 sq mi)Population (2011) • Total23,591 • Density23/km2 (60/sq mi)Time zoneUTC+6 (BST)WebsiteOfficial Map of Thanchi Thanchi (Bengali: থানচি) is an upazila of…

此條目需要补充更多来源。 (2021年7月4日)请协助補充多方面可靠来源以改善这篇条目,无法查证的内容可能會因為异议提出而被移除。致使用者:请搜索一下条目的标题(来源搜索:美国众议院 — 网页、新闻、书籍、学术、图像),以检查网络上是否存在该主题的更多可靠来源(判定指引)。 美國眾議院 United States House of Representatives第118届美国国会众议院徽章 众议院旗帜…

British debit card, 1988–2002 SwitchSwitch logoProduct typeDebit cardOwnerMasterCardCountryUnited KingdomIntroduced1988Discontinued2002Related brandsMaestro Switch was a debit card brand in the United Kingdom from 1988 until 2002. It was then merged with Maestro, which is owned by MasterCard. History Switch was launched in 1988 by Midland Bank, National Westminster Bank and The Royal Bank of Scotland as a multifunction cheque guarantee and cash card. The brand was merged with Maestro, an inter…
2020年夏季奥林匹克运动会波兰代表團波兰国旗IOC編碼POLNOC波蘭奧林匹克委員會網站olimpijski.pl(英文)(波兰文)2020年夏季奥林匹克运动会(東京)2021年7月23日至8月8日(受2019冠状病毒病疫情影响推迟,但仍保留原定名称)運動員206參賽項目24个大项旗手开幕式:帕维尔·科热尼奥夫斯基(游泳)和马娅·沃什乔夫斯卡(自行车)[1]闭幕式:卡罗利娜·纳亚(皮划艇)[2…
2020年夏季奥林匹克运动会波兰代表團波兰国旗IOC編碼POLNOC波蘭奧林匹克委員會網站olimpijski.pl(英文)(波兰文)2020年夏季奥林匹克运动会(東京)2021年7月23日至8月8日(受2019冠状病毒病疫情影响推迟,但仍保留原定名称)運動員206參賽項目24个大项旗手开幕式:帕维尔·科热尼奥夫斯基(游泳)和马娅·沃什乔夫斯卡(自行车)[1]闭幕式:卡罗利娜·纳亚(皮划艇)[2…

Tall, hairy species from Star Wars For other uses, see Wookie (disambiguation). This article describes a work or element of fiction in a primarily in-universe style. Please help rewrite it to explain the fiction more clearly and provide non-fictional perspective. (December 2020) (Learn how and when to remove this message) WookieeIn-universe informationHome worldKashyyykSub-racesSilverback WookieeDistinctionsBrown, white, or black furLanguageShyriiwook, Xaczik Wookiees (/ˈwʊkiːz/) are fictiona…

Welsh privateer This article includes a list of general references, but it lacks sufficient corresponding inline citations. Please help to improve this article by introducing more precise citations. (October 2021) (Learn how and when to remove this message) Map of the Darien Scheme, drawn in part with information from Lionel Wafer. Lionel Wafer (1640–1705) was a Welsh explorer, buccaneer and privateer. A ship's surgeon, Wafer made several voyages to the South Seas and visited Maritime Southeas…

Господарський суд Хмельницької областіКраїна УкраїнаВид господарський судІнстанція перша інстанціяЮрисдикція Хмельницька областьЗаснований 1991Суддів 16 + 4 вакантнихГолова Муха Микола ЄвгеновичНа посаді з 21 травня 2020[1]Розташування ХмельницькийАдреса майдан Незал�…

Artikel ini sebatang kara, artinya tidak ada artikel lain yang memiliki pranala balik ke halaman ini.Bantulah menambah pranala ke artikel ini dari artikel yang berhubungan atau coba peralatan pencari pranala.Tag ini diberikan pada Februari 2023. Rolf HädrichLahir(1931-04-24)24 April 1931Zwickau, JermanMeninggal29 Oktober 2000(2000-10-29) (umur 69)Hamburg, JermanPekerjaanSutradaraPenulis naskahTahun aktif1958-1989 Rolf Hädrich (24 April 1931 – 29 Oktober 2000) adalah s…

Russian mathematician This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed.Find sources: Boris Galerkin – news · newspapers · books · scholar · JSTOR (July 2020) (Learn how and when to remove this message) This article needs editing to comply with Wikipedia's Manual of Style. Please help improve the content. (February 2024) (Lear…

British royal regalia Crown JewelsSt Edward's Crown is the centrepiece of the British coronation regalia.OverviewCountryUnited KingdomLocationTower of London[a]Size≈ 140 objects[2]OldestCoronation Spoon (12th century)NewestCharles III's stole (2023)Stones23,578 including Cullinan I, Cullinan II, Koh-i-Noor, Black Prince's Ruby, Stuart Sapphire, St Edward's SapphireOwnerCharles III in right of the Crown[3]ManagersCrown JewellerRoyal Collection Tr…
Ethnic group in Saudi Arabia Ethnic group Australians in Saudi ArabiaTotal population5,000[1]Regions with significant populationsRiyadh · JeddahLanguagesEnglish (Australian) · ArabicReligionIslam, Roman Catholicism and Protestantism Australians in Saudi Arabia are a sizeable community consisting mainly of expatriates. Their population is estimated to be anywhere up to 5,000 with the majority based in major commercial centres such as Riyadh and Jeddah.[1&…

Douglas XP-48 adalah, pesawat tempur ringan kecil sayap rendah (low wing), dirancang oleh Douglas Aircraft pada tahun 1939 untuk evaluasi oleh Angkatan Udara Amerika Serikat. Dimaksudkan untuk didukung oleh mesin piston inline kecil, kontrak itu dibatalkan sebelum prototipe dapat dibangun, karena kekhawatiran Angkatan Darat tentang proyeksi kinerja pesawat.[1] Referensi ^ Douglas XP-48. National Museum of the United States Air Force. Accessed May 9 2010. Adcock, Al. OS2U Kingfisher in ac…

Halaman ini berisi artikel tentang film dokumenter tahun 1966. Untuk penggunaan lain, lihat Endless Summer (disambiguasi). The Endless SummerPoster rilis layar lebarSutradaraBruce BrownProduserBruce BrownDitulis olehBruce BrownPemeranMike HynsonRobert AugustMiki DoraNaratorBruce BrownPenata musikThe SandalsSinematograferBruce BrownPenyuntingBruce BrownDistributorCinema VMonterey MediaTanggal rilis 15 Juni 1966 (1966-06-15) Durasi95 menitNegaraAmerika SerikatBahasaInggrisAnggaran$50,00…

1812 battle during the French invasion of Russia This article is about the 1812 battle. For the World War II battles around Vyazma, see Battle of Bryansk, Vyazma airborne operation, and Operation Hannover. Battle of VyazmaPart of the French invasion of RussiaBattle of Vyazma, by Peter von HessDate3 November 1812 (22 Oct. by OS)LocationVyazma, Russian Empire55°12′N 34°15′E / 55.200°N 34.250°E / 55.200; 34.250Result Russian victoryBelligerents Russian Empire French …

Biografi ini memerlukan lebih banyak catatan kaki untuk pemastian. Bantulah untuk menambahkan referensi atau sumber tepercaya. Materi kontroversial atau trivial yang sumbernya tidak memadai atau tidak bisa dipercaya harus segera dihapus, khususnya jika berpotensi memfitnah.Cari sumber: Angga Dwimas Sasongko – berita · surat kabar · buku · cendekiawan · JSTOR (Februari 2023) (Pelajari cara dan kapan saatnya untuk menghapus pesan templat ini) Angga Dwimas S…

Бесплодная земляангл. The Waste Land[1] Жанр поэзия Автор Т. С. Элиот[1] Язык оригинала английский Дата первой публикации 1922[1] Издательство Horace Liveright[вд] Бесплодная земля (англ. The Waste Land) — поэма Томаса Стернза Элиота, которая считается одной из самых важных поэм …

Ariton Administration Pays États-Unis État Alabama Comté Dale Type de localité Town Code ZIP 36311 Code FIPS 01-02428 GNIS 151663 Indicatif(s) téléphonique(s) local (locaux) 334 Démographie Population 764 hab. (2010) Densité 58 hab./km2 Géographie Coordonnées 31° 35′ 54″ nord, 85° 43′ 08″ ouest Altitude 281 m Superficie 1 318 ha = 13,18 km2 · dont terre 13,18 km2 (100 %) · dont eau 0 k…