Mix network
|
Read other articles:

1793 battle during the War of the First Coalition Battle of HondschootePart of the Flanders campaign in the War of the First CoalitionThe Battle of HondschooteDate6–8 September 1793LocationHondschoote, French Republic50°58′49″N 2°35′10″E / 50.9803°N 2.5861°E / 50.9803; 2.5861Result French victoryBelligerents French Republic Great Britain Hanover Hesse-KasselCommanders and leaders Jean Nicolas Houchard Jean-Baptiste Jourdan (WIA) Duke of York Heinrich Wi…

Tunisian basketball player (born 1986) Salah Mejriصالح الماجريMejri while playing with Obradoiro in May 2013Personal informationBorn (1986-06-15) June 15, 1986 (age 37)Jendouba, TunisiaNationalityTunisianListed height7 ft 2 in (2.18 m)Listed weight235 lb (107 kg)Career informationNBA draft2008: undraftedPlaying career2006–2023PositionCenterNumber50Career history2006–2010Étoile Sportive du Sahel2010–2012Antwerp Giants2012–2013Obradoiro CAB2013–2…

此條目可参照英語維基百科相應條目来扩充。 (2021年5月6日)若您熟悉来源语言和主题,请协助参考外语维基百科扩充条目。请勿直接提交机械翻译,也不要翻译不可靠、低品质内容。依版权协议,译文需在编辑摘要注明来源,或于讨论页顶部标记{{Translated page}}标签。 约翰斯顿环礁Kalama Atoll 美國本土外小島嶼 Johnston Atoll 旗幟颂歌:《星條旗》The Star-Spangled Banner約翰斯頓環礁地�…

土库曼斯坦总统土库曼斯坦国徽土库曼斯坦总统旗現任谢尔达尔·别尔德穆哈梅多夫自2022年3月19日官邸阿什哈巴德总统府(Oguzkhan Presidential Palace)機關所在地阿什哈巴德任命者直接选举任期7年,可连选连任首任萨帕尔穆拉特·尼亚佐夫设立1991年10月27日 土库曼斯坦土库曼斯坦政府与政治 国家政府 土库曼斯坦宪法 国旗 国徽 国歌 立法機關(英语:National Council of Turkmenistan) 土�…

Ethnic groups in the United States Not to be confused with Romani Americans. Romanian AmericansTotal population464,814 (2019)[1][2] 1,200,000 (other estimates in 2019)[3]Regions with significant populations New York City Metropolitan Area New Jersey Ohio Colorado California Illinois Michigan Maryland Wisconsin Minnesota Florida Pennsylvania Georgia Iowa Indiana Tennessee Texas Massachusetts Oregon Hawaii District of Columbia Southwest U.S.[4][5][6]…

Halaman ini memuat daftar perdana menteri Trinidad dan Tobago. Bisa lihat juga daftar Gubernur Trinidad dan Tobago, daftar Gubernur Jenderal Trinidad dan Tobago, dan daftar Presiden Trinidad dan Tobago. Ketua Menteri Trinidad dan Tobago (1950-1959) # Nama Gambar Mulai Sampai Partai 1 Albert Gomes 1950 1956 POPPG 2 Eric Williams 1956 1959 PNM Premier Trinidad dan Tobago (1959-1962) # Nama Gambar Mulai Sampai Partai 1 Eric Williams 1959 1962 PNM Perdana Menteri Trinidad dan Tobago (1962-Sekarang) …

British linguist Not to be confused with James Elphinstone. James Elphinston James Elphinston (December 6, 1721 – October 8, 1809) was a well noted 18th-century Scottish educator, orthographer, phonologist and linguistics expert. Life Elphinston was a good friend of Samuel Johnson as stated in Life of Samuel Johnson, LL.D. (1904, Oxford edition), Chapter IV [1750], and tutor of Alexander James Dallas. Mr. James Elphinston, who has since published various works, and who was ever esteemed by…

20 [Twenty]Album studio karya F.T. IslandDirilis16 Mei 2012 (2012-05-16)Direkam2011–12South KoreaGenreRockDurasi44:02BahasaJapaneseLabelWarner Music JapanKronologi F.T. Island Grown-Up(2012)Grown-Up2012 20 [Twenty](2012) Five Treasure Box(2012)Five Treasure Box2012 Singel dalam album 20 Let It Go!Dirilis: 27 Juli 2011 (2011-07-27) DistanceDirilis: 30 November 2011 (2011-11-30) NeverlandDirilis: 18 April 2012 (2012-04-18) Templat:Contains Japanese text 20 [Twenty] (ditul…

Medieval kingdom in Punjab Langah Sultanate1445–1526Approximate territory of the Langah Sultanate at its greatest extent, circa 1475 CE.[1]StatusSultanateCapitalMultanSpoken languagesPunjabi (dynastic), BalochiReligion IslamGovernmentHereditary monarchySultan Historical eraLate medieval period• Established 1445• Disestablished 1526 Preceded by Succeeded by Sayyid dynasty Mughal Empire Today part ofPakistan The Langah Sultanate, also known as the Sultanate of Multan, …

Australian Paralympic swimmer Paige Leonhardt2016 Australian Paralympic team portraitPersonal informationFull namePaige LeonhardtNationalityAustralia/CanadaBorn (2000-09-21) 21 September 2000 (age 23)NSW, AustraliaSportSportSwimmingClassificationsS14ClubYeronga Park Swimming ClubCollege teamCarmel College, Thornlands QLDCoachRobert Van Der Zant Medal record Women's paralympic swimming Representing Australia Paralympic Games 2020 Tokyo 100 m butterfly S14 World Para Swimming …
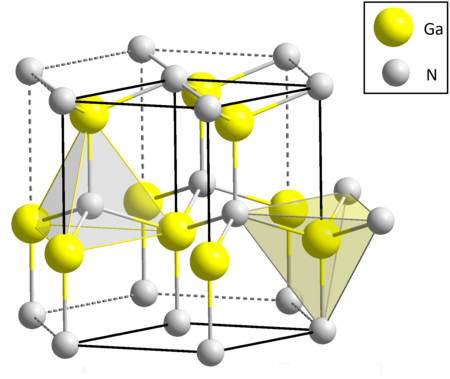
This article is about Gallium nitride, the chemical compound. For other uses, see Gan. Gallium nitride Names IUPAC name Gallium nitride Other names gallium(III) nitride Identifiers CAS Number 25617-97-4 Y 3D model (JSmol) Interactive imageInteractive image ChemSpider 105057 Y ECHA InfoCard 100.042.830 PubChem CID LW9640000 = LW9640000 UNII 1R9CC3P9VL Y CompTox Dashboard (EPA) DTXSID2067111 InChI InChI=1S/Ga.N YKey: JMASRVWKEDWRBT-UHFFFAOYSA-N YInChI=1/Ga.N/rGaN/c1-2…

圣若泽São José市镇 旗幟徽章圣若泽在巴西的位置坐标:27°36′54″S 48°37′40″W / 27.615°S 48.6278°W / -27.615; -48.6278国家巴西州圣卡塔琳娜州面积 • 总计113 平方公里(44 平方英里)海拔8 公尺(26 英尺)人口(2008) • 總計196,887人 • 密度1,742人/平方公里(4,513人/平方英里) 圣若泽(葡萄牙语:São José)是巴西圣卡塔琳娜�…

English lawyer and politician 1781–1851 The Right HonourableThe Earl of CottenhamPCLord Cottenham wearing ceremonial robes when presiding in the House of Lords as Lord Chancellor. Detail of a painting by Charles Robert Leslie.Lord High Chancellor of Great BritainIn office16 January 1836 – 30 August 1841MonarchsWilliam IV VictoriaPrime MinisterThe Viscount MelbournePreceded byIn CommissionSucceeded byThe Lord LyndhurstIn office6 July 1846 – 19 June 1850MonarchVictoriaPrime…

Open Cluster in the constellation of Scorpius NGC 6231NGC 6231 (top) with Zeta2 and Zeta1 Scorpii (bottom)Observation data (J2000.0 epoch)Right ascension16h 54mDeclination−41° 48′Distance5,600±400 ly (1,700±130 parsec[1])Apparent magnitude (V)2.6Apparent dimensions (V)15.0′Physical characteristicsEstimated age2–7 million years[2][3]Other designationsNGC 6171, Caldwell 76, Collinder 315, Melotte 153, De Cheseaux 9, Dunlop 499, Ha. I.…

Scottish golfer Bob FergusonBob Ferguson, c. 1903Personal informationFull nameRobert FergusonBornc. 1846Musselburgh, ScotlandDied19 May 1915 (aged 69)Musselburgh, ScotlandSporting nationality ScotlandCareerStatusProfessionalBest results in major championships(wins: 3)The Open ChampionshipWon: 1880, 1881, 1882 Robert Ferguson (c. 1846 – 19 May 1915) was a Scottish professional golfer who was one of the top players from the mid-1860s into the 1880s. He won a hat-trick of c…

2016 Paralympics Parade of Nations, Luxembourg. People with disability in Luxembourg have some legal protections from discrimination and their needs can be provided through various government policies. Students with disabilities have a fairly good rate of completing school compared to peers without a disability. Luxembourg signed onto the Convention on the Rights of Persons with Disabilities on March 30, 2007. Much of the country is accessible, however, there are no legal provisions for reasonab…

Các hệ thống kinh tế Kinh tế tư bản chủ nghĩa Kinh tế xã hội chủ nghĩa Kinh tế thị trường Kinh tế kế hoạch Kinh tế hỗn hợp Chủ nghĩa xã hội thị trường Kinh tế thị trường định hướng xã hội chủ nghĩa Kinh tế thị trường xã hội Kinh tế chuyển đổi Kinh tế mở Kinh tế khép kín Kinh tế tự cung tự cấp Kinh tế hàng hóa Kinh tế tiền tệ Quản trị kinh doanh • Công ty •&…

Eparki Tuckalayதக்கலை மறைமாவட்டத்தின்LokasiNegaraIndiaProvinsi gerejawiEparki Agung ChanganasseryMetropolitEparki Agung ChanganasseryStatistikLuas1.794 km2 (693 sq mi)Populasi- Total- Katolik(per 2010)2.071.25829,673 (1.4%)InformasiRitusSiro-MalabarKatedralKatedral di ThuckalayPelindungBunda Kristus dan Citra GerejaSanto GregoriusKepemimpinan kiniPausFransiskusUskup agung mayorMar George AlencherryUskupMar George Rajend…

Ini adalah nama Korea; marganya adalah Kim. Kim Byeong-okKim Byeong-ok dalam konferensi pers serial drama The Sound of Your Heart tahun 2016Lahir11 Oktober 1960 (umur 63)Korea SelatanPekerjaanAktorNama KoreaHangul김병옥 Alih AksaraGim Byeong-okMcCune–ReischauerKim Pyŏng-ok Kim Byeong-ok (Hangul: 김병옥; lahir 11 Oktober 1960) merupakan seorang aktor Korea Selatan. Ia dikenal sebagai aktor pendukung dalam film Oldboy.[1] Filmografi Film Operation Chromite (2016) A V…

Colombian painter and sculptor (1932–2023) In this Spanish name, the first or paternal surname is Botero and the second or maternal family name is Angulo. For the Colombian politician, see Fernando Botero Zea. Fernando BoteroBotero in 2018BornFernando Botero Angulo[1](1932-04-19)19 April 1932Medellín, ColombiaDied15 September 2023(2023-09-15) (aged 91)Monte Carlo, MonacoKnown forPaintersculptorNotable work Mona Lisa, Age Twelve (1959) Pope Leo X (after Raphael) (1964…























